Main
Background
Methods
Results
Conclusions
Group Members
Results
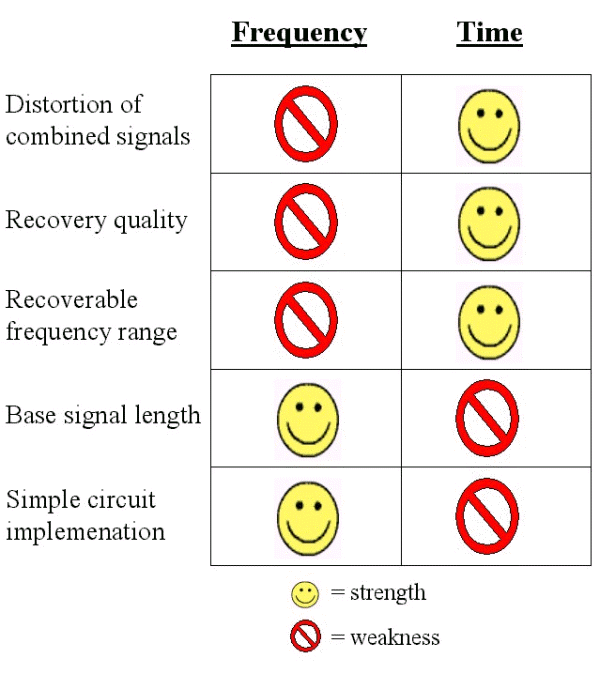
After completing experiments in both the time and frequency
domains, we found that signals of various qualities can be used
simultaneously, one for the base and one for the message. We also
discovered some of the strengths and weaknesses of doing
steganograpy in each domain.
A few of the strengths of the frequency domain are that the base
only needs to have the same number of samples as the message.
This means that a longer message can be hidden in a given base
signal than in the time domain. Also, this algorithm is easy to
implement in simple circuit elements that we already know about.
Finally, the frequency domain implementation is also much less
likely than the time domain to be affected by errors that occur
during transmission. On the down side, this algorithm has a lot
of distortion in the combined signal. This includes an audible
high-pitched cosine that occurs from the modulation. Also,
because of the filtering that occurs, the message signal has a
limited frequency range and low recovery quality.
When steganography was imlplemented in the time domain, we
found that it had strengths and weaknesses opposite of those in
the frequency domain. There was almost no distortion in the
combined signals if only a quarter of the base signal's bits were
used to hide the signal. Also, the message could be perfectly
recovered and had no frequency limitations. The disadvantages
are that the base signalneeds to be longer than the message (see
time domain methods) and that without DSP chips, this is harder
to implement in circuitry. In addition, this method is extremely
easy to corrupt during transmission. This could be resolved by
encoding the message using hamming code to detect errors. If a
hash table was used to determine which samples had bits replaced,
this could be a very effective method for digital watermarking.